Effectively battling threats requires actionable intelligence, something many organizations lack today. Typically, compromises or threats are only discovered sometime after an incident occurs, turning what should have been a defense into incident response. That lack of quick discovery potentially creates dark areas in IT, where lateral attacks, data exfiltration and other compromises can go on for days, weeks or even months.
What’s more, the damage that occurs between an active threat and its discovery can be business-ending, especially for small- and medium-size enterprises. According to IBM, the average cost of a data breach in 2020 was $3.86 million, and the average lifecycle of a breach was 280 days from identification to containment. Simply put, the high costs of undetected compromises and breaches are things that most organizations cannot withstand.
Miami, Florida-based Lumu aims to put an end to that lack of threat discovery with an innovative platform that constantly monitors IT infrastructures for compromises, allowing action to be taken quickly. Lumu’s mantra is one of providing cybersecurity professionals with actionable information about compromises, while also identifying the so-called dark areas of IT to help IT staffers harden their defenses.
A closer look at Lumu
Lumu is a platform-based approach for continuous compromise assessment that leverages metadata to identify confirmed compromise incidents. The platform uses multiple data sources to understand the behavior of enterprise networks, which in turn can be used as an evidence-based method to identify areas subject to threats and compromises. Meanwhile, it offers security professionals unique insights into the level of compromise experienced on the network.
Lumu is available in three different flavors:
- Lumu Free is offered as a free service, and it has limited capabilities. Lumu Free offers limited visibility of confirmed IoCs (Indicator of Compromise), access to the Lumu Portal, real-time DNS ingestion, continuous compromise assessments of as many as 10 gateways.
- Lumu OnDemand adds additional features, such as ad-hoc compromise assessment, manual ingestion of numerous metadata sources and actionable insights, along with cybersecurity posture recommendations and information on how to mitigate detected compromises.
- Lumu Insights, the company’s premier service, offers additional features that should prove very valuable to any team responsible for hunting for threats and dealing with compromises. That service adds detailed visibility into IoCs, as well as network traffic groupings. Network metadata ingestion becomes automated and is performed in real-time. Other features include an unlimited virtual appliance data collector, attack pattern recognition, extensive reporting, and many other novel features.
Hands-on with Lumu Insights
Lumu Insights is the top-tier product offered by the company and as such offers the most extensive feature set. Lumu Insights is deployed using a virtual appliance, which is able to collect data from the network’s extended perimeter. The company also offers agents for most operating systems, which in turn gives additional insights into endpoints–including those that are remote.
[To see a larger view of this image, click on it and select “Open in New Tab.”]
Lumu Insights is able to gather metadata from the local network as well as the cloud, and also from remote endpoints. The Lumu virtual appliance runs on existing hypervisors and is able to gather DNS queries as they traverse the network, while also collecting netflow information and log data. The platform collects a wide range of network metadata, including DNS, netflows, proxy and firewall access logs and Spambox. It can automatically analyze and normalize all activity to discover any outliers and report that information back to IT professionals.
Real-time DNS ingestion proves to be one of the most critical capabilities of the product, since DNS analysis adds much-needed context to network traffic. Ultimately, Lumu’s novel approach to collecting metadata enables the platform to take a deeper look into network operations across network metadata and provide the context that threat hunters need to be effective in their roles.
The platform also offers advanced capabilities, such as attack pattern recognition, network traffic grouping and drill-down capabilities, two years of data retention, the ability to ingest existing threat intelligence, playback capabilities and customizable reports.
In practice, Lumu Insights sits quietly on the network perimeter, and along with the endpoint agents, gathers and analyzes data. However, the real power of the platform comes in the form of what it does with that data and how it creates insights in real time, so that IT staffers can take action quickly if an attack or compromise happens.
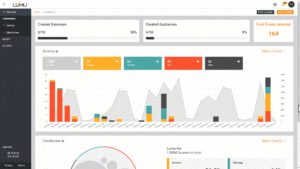
The Lumu Portal functions as the primary dashboard and offers a visual representation of the potential threat and compromise environment. The real-time analytics functions by using AI algorithms to compare network metadata in real time to correlate the information against known IoCs, creating an instant assessment of the level of risk.
That information is displayed as alerts on the dashboard and is also available in analytical reports, as well as electronic notices to keep administrators in the loop and encourage proactive actions for maintaining cyber hygiene. One of the more interesting features is the platform’s ability to group network traffic and then allow administrators to drill down into that traffic. Since the platform can collect as much as two years of data, the ability to group network traffic and further analyze it proves critical for forensics tasks.
What’s more, the platform offers playback capabilities, where administrators can step through recorded network activity to better understand exactly what happened during a breach or attack. The insights provided by playback give administrators the opportunity to assess policies and define new rules to help limit attack vectors.
With Lumu Insights, it seems to be all about visibility into the network. The platform allows administrators to focus on compromise assessment and track compromised assets, while also giving actionable insights to administrators, which in turn amounts to full network visibility from the perspective of what is at risk. The platform proves intuitive and provides detailed reports that illustrate the risk presented to assets, while also functioning in real-time.
Conclusions
Lumu Insights is a security platform that can give businesses the upper hand when dealing with evolving threats and compromises, while also discovering the dark areas of the network which potentially become new threat vectors. Lumu Insights offers additional value to cybersecurity teams by working with existing threat intelligence platforms and offers detailed visibility into IoCs.
As cyberthreats evolve, products like Lumu Insights will become critical to cyber operations, especially since the past has shown that compromises and threats can exist for months before discovery. Businesses need to take threat hunting and remediation more seriously and Lumu Insights may very well be the tool to accomplish that.
Lumu offers a free version of the platform that allows anyone to test the service. The premium version, Lumu Insights starts at $64 per asset per year, more information on pricing, features, and other options can be found by following this link.
Frank Ohlhorst is a veteran IT product reviewer and analyst who has been an eWEEK regular for many years.